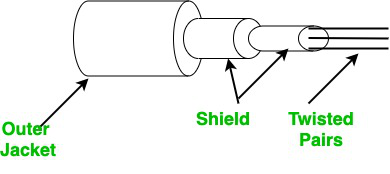
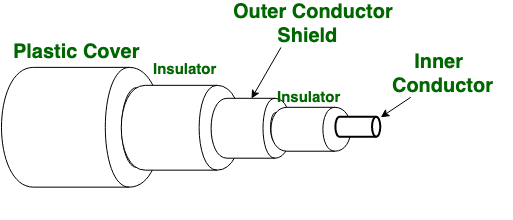
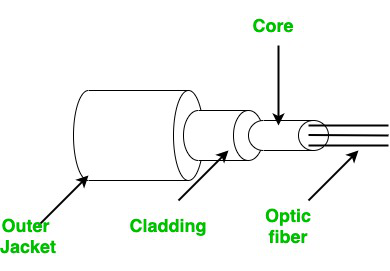
We are living in a world, where we can connect with friends within seconds no matter how far they are. But this was not possible in earlier days. We all have heard and read that earlier communication is very tough as sending a letter will require many days and sometimes months. Today is not a case we have different types of medium which can transmit our message very quickly. In this article, we will learn about transmission medium and after wireless communication. Now, what is a transmission medium? Basically, it transmits signals or messages from one computer to another computer. The transmission medium is further divided into two types: Wired or Guided transmission media ( e.g.: Twisted pair cable, Ethernet cable, Coaxial cable, and Optical fiber) and other is wireless or unguided transmission medium (e.g.: Infrared, Radio link, Microwave link, Satellite link, Bluetooth, WIFI ).
In this article, we are more concerned about wireless communication. So, let’s begin understanding wireless communication.
Wireless Communication
Wireless communication is also referred to as Unguided Media or Unbounded transmission media. In this mode, no physical medium is required for the transmission of electromagnetic signals. In wireless communication, we can transfer our message through the air, water or vacuum i.e. Infrared, Radio wave, Microwave wave. So, we don’t worry about the cables or any material to transfer messages, as we can send out a message without and medium.
Wireless communication has advantages and also have disadvantages like it is less secure if we talk about security.
Features
- No physical medium is required for transmission.
- It can carry signals through air, water, or vacuum.
- It can travel large distances but it is also less secure.
Let’s discuss some of its types:-
Infrared
Infrared is used for short-range communication like TV remotes, mobile phones, personal computers etc. In science, the Infrared is part of a spectrum that is not visible to the human eye. The limitation of infrared rays is that they cannot penetrate any obstacles and can only use for short-range. Also, Infrared is used in night vision cameras as it has thermal properties. The frequency range of infrared rays 300GHz – 400THz
Uses:
As we have already have discussed they are used in TV remotes, Pc devices like mice, and keyboards.
Advantage and Disadvantage:
If we talk about the merit part of infrared then we can say Infrared is one of the secure wireless communication mediums as it is used for short-range. Also, unlike other wireless mediums, infrared is quite inexpensive, and this is some reason it is used in many electronic devices.
Now, let’s talk about the disadvantaged part of Infrared waves so they can only be used in short-range communication. Also, they cannot penetrate any obstacles like walls or any building.
Radio Waves
So we have seen the limitation of infrared waves, so here’s another wireless communication that does not have limitations like infrared. Here we are discussing radio waves. that can travel large distances as well as can penetrate any wall ( Omni-directional, these waves can move in all directions). These are easy to generate and can penetrate through buildings. The requirement of radio waves is antennas, sending antennas where one can transmit its message and the other is receiving antennas. The frequency range of radio waves:3KHz – 1GHz. Also, radio waves of frequency 300KHz-30MHz can travel long distances. Moreover, they are Susceptible to interference meaning they can penetrate any walls.
Uses:
Radio waves are used in AM and FM radios, and cordless phones. Also, some private and government organization reserves certain radio frequencies for direct communication.
Advantage and Disadvantage:
Radio waves have some advantages like they can travel long distances in all directions and can pass through any obstacles, and since they are wireless communication mediums so there is no need of digging and spreading wires. But, yes radio waves have some disadvantages too like radio waves are not effective in bad weather conditions, and they are less secure as they can travel large distances.
Microwaves
Microwaves are a line of sight transmission, meaning both the antennas sending and receiving should be properly aligned. Also, the distance covered by the signal is directly proportional to the height of the antenna. Microwaves have a frequency Range between 1GHz – 300GHz. Basically, we used Microwaves in mobile phones communication and television distribution.
Unlike radio waves, they are unidirectional, as they can move in only one direction, and therefore it is used in point-to-point communication or unicast communication such as radar and satellite.
Uses:
Microwaves are used in mobile phones communication and television distribution.
Advantage and Disadvantage:
If we talk about the advantages of microwaves then we say that it is a very fast way of communication, that can carry 25000 voice channels at the same time. Also, it is a wireless communication medium so there is no need of digging and spreading wires.
Now demerits of microwaves are the first expense, their installation and maintenance are very expensive. that turns this into a very expensive mode of communication. Moreover, Microwaves are also not very effective in bad weather conditions.