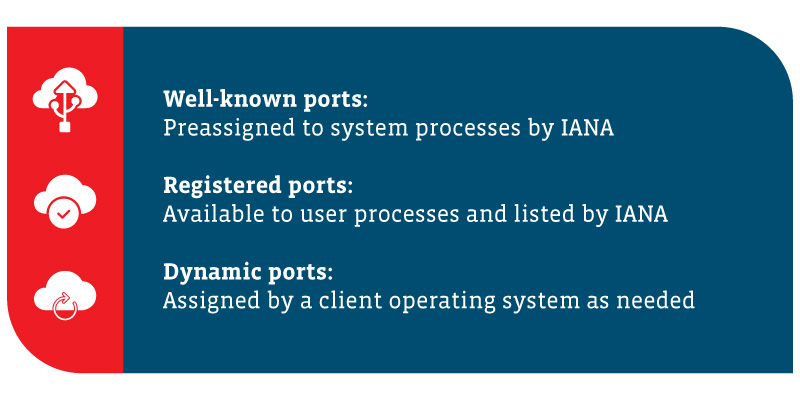
Services and apps that float among the cloud are similar in many ways to the services and apps that remain grounded in your on-premises infrastructure. Take cloud-based web apps and directory services, for example. Many will use the same ports and protocols that are used by their on-premise counterparts. Management tools, whether CSP-based, third-party or those built by your IT team, will also utilize port and protocol requirements.
If you decide to make the jump from the ground to the cloud, you will need to review your ports to determine what needs to be based in the cloud and what needs to remain housed on your own infrastructure. Take a close look at what needs internet access, in order to communicate with outside services or apps, and what type of access is required from inside the cloud.
Once you narrow it down, you can configure firewalls and set the necessary filters to ensure your cloud network will remain secure. As you work to deploy your cloud network, make sure you consult the following resources:
- App and service configuration guides to identify the necessary ports and protocols each one uses.
- CSP security and deployment guides or white papers to locate the ports and protocols you need to access cloud services such as websites, databases, directory services and so on.
- Third-party deployment guides that are similar to the cloud network you are implementing.
- Your own (yes, your own) documentation to reference your firewall, routing, and other related information that could help you understand your own port and protocol usage. It will be tough to implement a successful cloud deployment if you have no idea from where you are jumping.
- If the fates forbid you from uncovering what ports and protocols are used by a legacy application that you want moved to the cloud, you might want to gather some helpful tools such as a port scanner or protocol analyzer to unlock the guarded secrets of your predecessors.
Before launching any cloud network, take a look through all your apps and services to ensure all ports and protocols are toeing the line.